Introduction
Customer data is imported into bi(OS) through various mechanisms, some requiring us to expose a public HTTP endpoint. These endpoints are protected against bots. We also record these attack vectors within bi(OS). We built this multi-cloud bot detection capability in 4 weeks using this data. Further, this dynamic list of bots is also made available to all our customers.
A Tale of Multi-cloud Bots
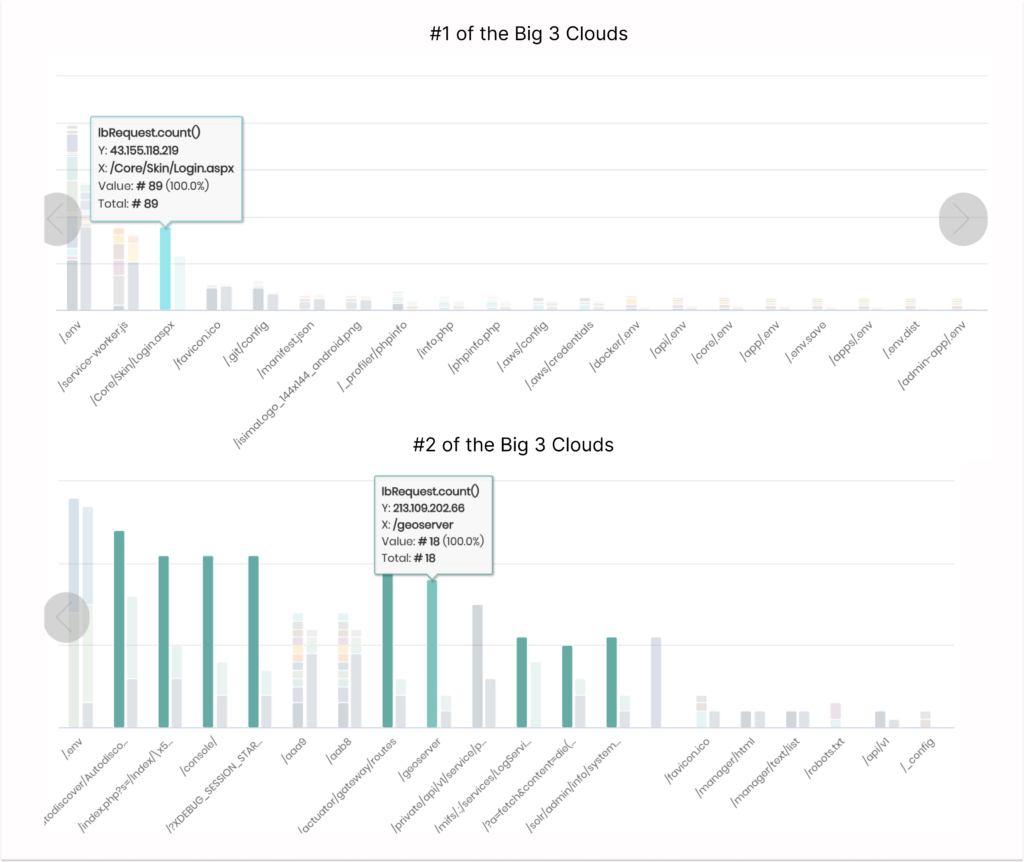
Above is a real-time bi(OS) visualization of various bots “probing” for vulnerabilities and their IP addresses across two of the big 3 public clouds. A few differences stand out:
- Bots differ significantly in intensity and use various IP addresses.
- Some bots go broad and probe for the “usual suspects”. Others try to go deep and check for the same vulnerability with a large-scale attack.
- The bot farms targeting the big 3 public clouds differ non-trivially.
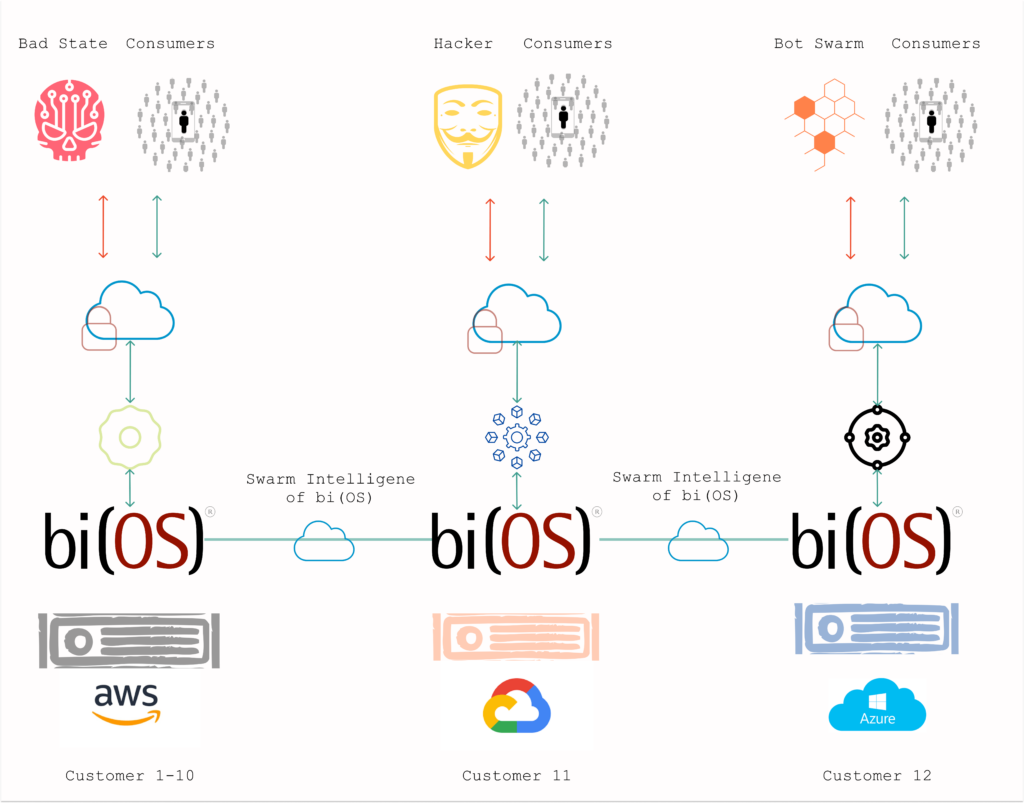
Multi-cloud Bot Prevention
Armed with this data, Isima’s engineers built a capability that mimics swarm intelligence across clouds to thwart these bots. Bot detection capability is present in every installation of bi(OS), and the findings are broadcast to all installations of bi(OS). Each bi(OS) installation merges its own data with the rest. The end result is a dynamic multi-cloud Bot prevention mechanism that keeps learning and improving. Every update made to the blacklist is audited, and every blocked access is logged.
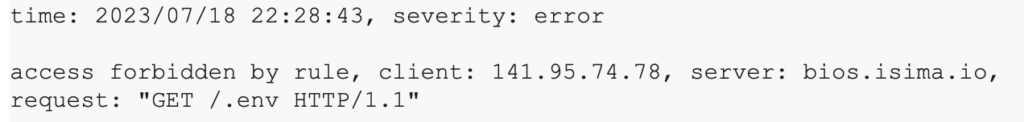
Let’s all share the bad (actors)
This data about the bad actors is made available to all customers. They can now use this data to help perform bot prevention for other applications, improve traffic quality for personalization micro-services, or inform their InfoSec and privacy team to block access across the network for these bots.
Conclusion
Security is everyone’s responsibility. As the attack vectors grow, cooperation amongst applications, teams, and organizations is the only way to outcompete attackers. bi(OS) ships with robust, pioneering multi-cloud bot prevention capabilities. Further, it provides visibility into the attack vectors that encourage cooperation without a forklift. Bots beware, bi(OS) is the silent guardian.
1 Hour to BI, 1 Day to AI, and 1 Week to API. To get started for free, click here.
